
On Friday May 12, the world faced a massive coordinated ransomware attack, also known as ‘WannaCry’ and ‘Wanna Cryptor’. Specific malware is transferred via email to Microsoft users, resulting in Windows computers being blocked with all the contents encrypted. Victims are demanded to pay hundreds of dollars to get back access to their files. So far, around 100 countries have been exposed to the cyberattack, including such institutions as FedEx, Russian Interior Ministry, numerous UK hospitals, China schools, etc. hit. According to online security researchers, many people have already given in to pay between $300-600 in bitcoins to the hackers each.
The story in detail
Last August, it was announced that some of the important NSA hacking tools were stolen by the Shadow Brokers, allowing to remotely penetrate computer systems. One of them, called ‘Eternal Blue’, is an exploit subsequently applied within WannaCry attack to deliver the ransomware to Windows computer machines, running the file sharing protocol Server Message Block (SMBv1), and therefore take control over the systems. Actually, ‘Eternal Blue’ is also a name for a zero-day vulnerability, which Microsoft was not warned about in advance for unknown reasons.
A month ago, the stolen stash of NSA documents was reported to leak online. Prior to this alarming news, Microsoft had unknowingly fixed the bug, related to External Blue, with a target security update (MS17-010). However, many computers failed to timely install the released patch and thus use the introduced protection: this is because some users purposefully disable Windows updates, added by a lot of time it takes software updates to get accepted by tech departments of large institutions.
On Friday afternoon, the National Health Service of the UK reported a number of hospital systems to have gone down crashing. The virus was spreading quickly, hitting around 40 hospitals in 3 hours. Soon it turned out that many other institutions around the world fell victims of the similar ransomware attacks.
Files with the following extensions get encrypted by the malware:
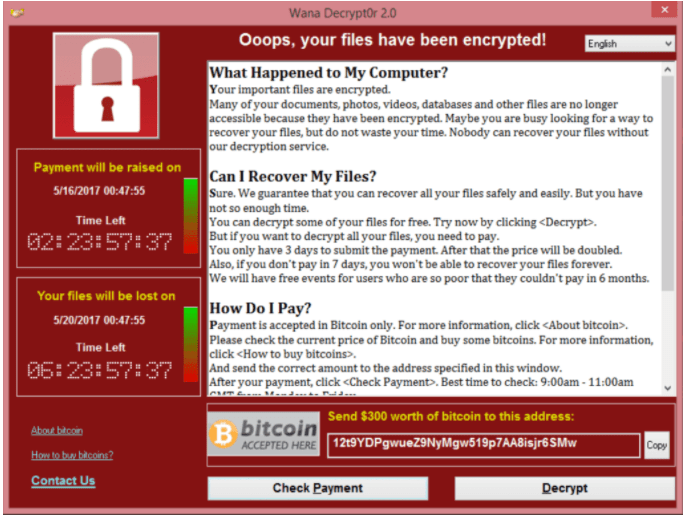
And here is a message that pops up after the attack:
By now, WannaCry attack has been halted by a security expert from the UK. Thanks to his findings related to a WannaCryptor kill switch feature, millions of users now have time to download and install the Windows special update. Unfortunately, it is not clear how soon the hackers will update the kill switch, which is why the attack is not over yet. Moreover, another Windows zero-day exploit has been revealed spreading on the Internet by the Spanish security firm CERT.
How to get secured
Microsoft was in a hurry to inform users of the security update and posted a special guidance on how to deal with the ransomware attack late on Friday. We advise you to check it out.
First and utmost, make sure that you have updated your Windows system (the necessary package is MS17-010). This can be done manually: go to Control Panel -> System and Security -> Windows Updates.
Backup all the important data. For that, you can use an external hard drive or cloud storage space.
Be exceptionally vigilant: do not open doubtful emails, avoid proceeding to unknown links or opening suspicious files.
Remember to keep the firewall activated and updated too, check all the incoming files that bring up firewall security warning messages carefully.
Worth mentioning, a VPN will not protect you from the attack, since it only encrypts your activity, but does not prevent loading potentially harmful files. BUT a VPN is likely to provide a certain amount of countermeasure against malware targeting online access points, especially when browsing via public Wi-Fi.
Finally, under no circumstances should you pay to the hackers! There is no guarantee that money will actually bring your ransomware attacked files back. Instead, look for professional tech assistance.